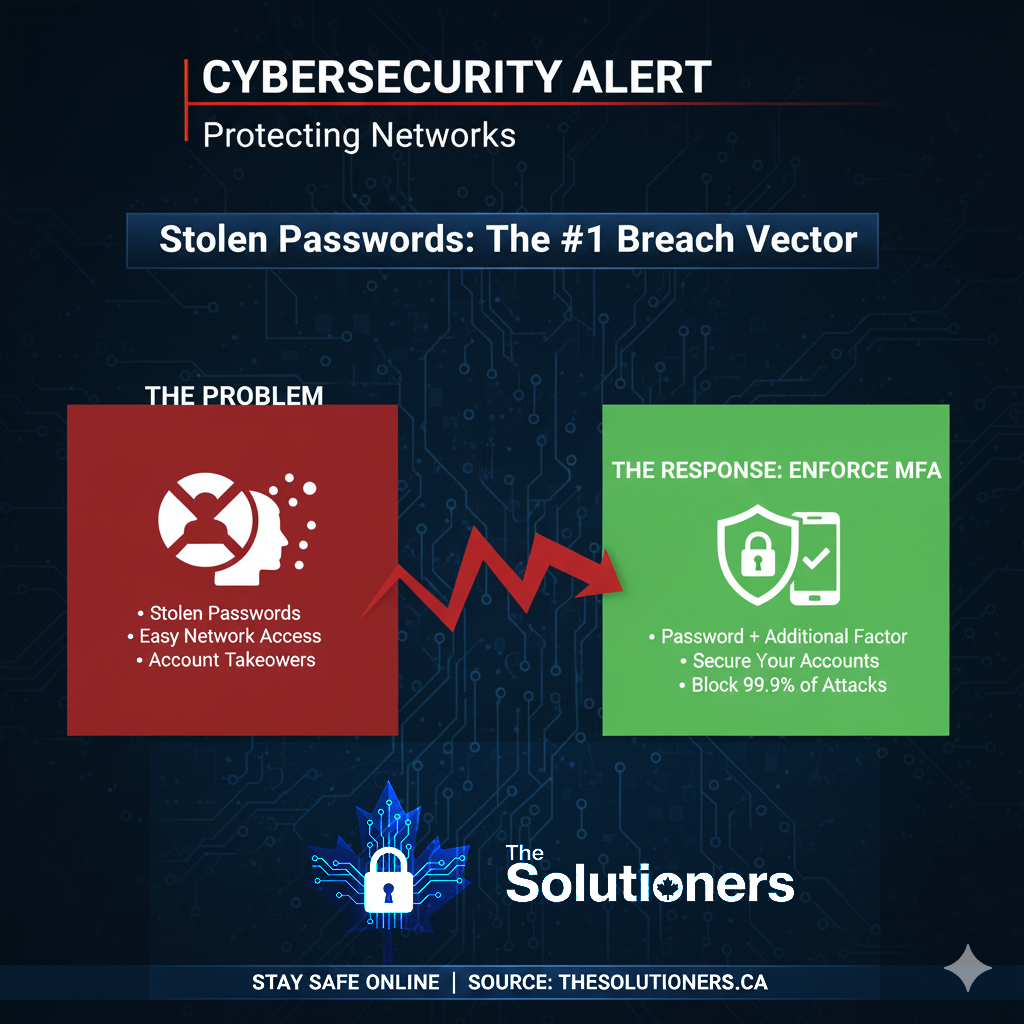
1. Enforce Multi-Factor Authentication (MFA)
MFA is the single most effective control against account compromise. Enable it on email, VPNs, and all cloud applications.
Prefer app-based authenticators (like Microsoft Authenticator) or hardware keys over SMS, which can be intercepted.
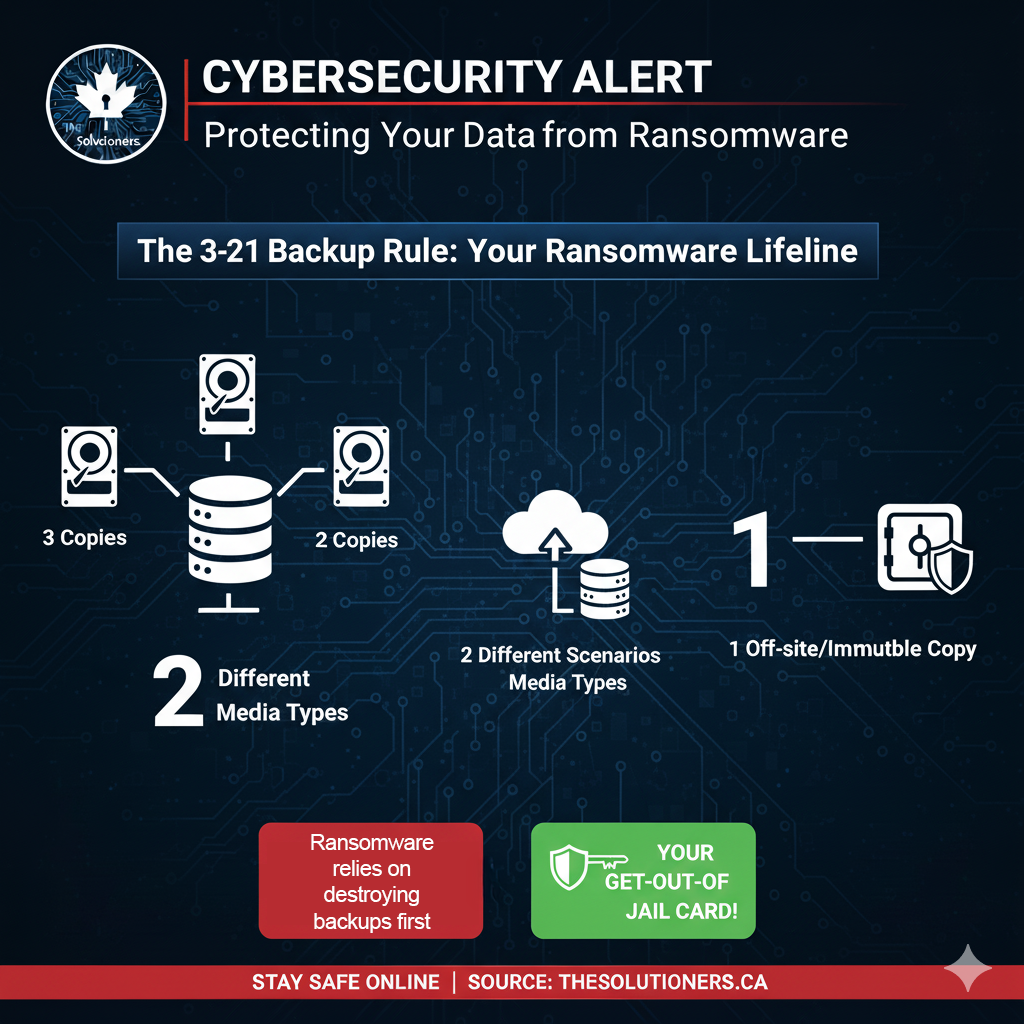
2. Secure Your Backups
Ransomware attackers target backups to force payment. Follow the 3-2-1 rule: 3 copies of data, 2 different media types, 1 offsite (immutable).
Regularly test your restores to ensure business continuity.
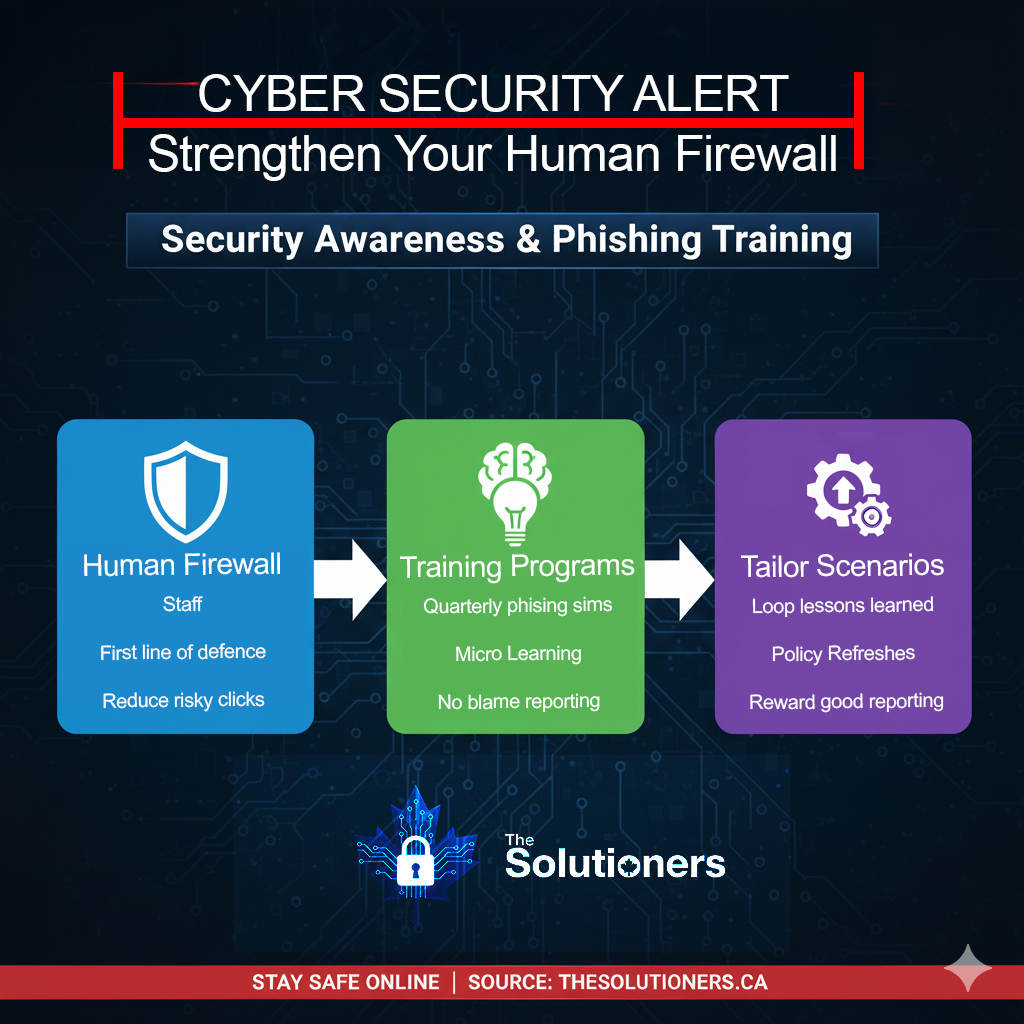
3. Train Your Team
Your employees are your first line of defense. Regular security awareness training and phishing simulations help them spot and stop attacks.
Foster a culture where reporting suspicious activity is encouraged, not punished.
Bonus: keep systems patched
- Automate updates for operating systems and browsers.
- Prioritize patching internet-facing systems.
